We do cutting-edge research on bandit problems, reinforcement learning, artificial intelligence for medicine,, multi-agent systems, stream mining, influence maximization, and cognitive communications. Our group is led by Prof. Cem Tekin.
News
October 2025: Our paper has been published in Transactions on Machine Learning Research: Andi Nika, Sepehr Elahi, Cem Tekin, "Contextual Combinatorial Bandits With Changing Action Sets Via Gaussian Processes".
September 2025: Our paper has been accepted to NeurIPS 2025 Workshop: AI and ML for Next-Generation Wireless Communications and Networking: Emre Özyıldırım, Barış Yaycı, Umut Eren Akturk, Cem Tekin, "Satisficing with Binary Feedback: Multi-User mmWave Beam and Rate Adaptation via Combinatorial Bandits".
September 2025: Our paper has been accepted to NeurIPS 2025: Artun Saday, Yaşar Cahit Yıldırım, Cem Tekin, "Robust Satisficing Gaussian Process Bandits Under Adversarial Attacks".
September 2025: Our paper has been accepted to NeurIPS 2025 as Spotlight Paper (13% of accepted papers): Eray Can Elumar, Cem Tekin, Osman Yağan, "Cost-aware LLM-based Online Dataset Annotation".
August 2025: Invited to serve as Associate Editor for IEEE Transactions on Networking.
August 2025: Invited to serve as Area Chair for AISTATS 2026.
August 2025: Our paper has been published in Transactions on Machine Learning Research: Andi Nika, Sepehr Elahi, Çağın Ararat, Cem Tekin, "Beyond Grids: Multi-objective Bayesian Optimization With Adaptive Discretization".
July 2025: Invited to serve as Senior Program Committee Member for AAAI-26-AIA.
July 2025: Our paper was presented at ICML 2025: Yiğit Narter, Alihan Hüyük, Mihaela van der Schaar, Cem Tekin, "Unified Screening for Multiple Diseases".
January 2025: Our paper has been published in IEEE Transactions on Artificial Intelligence: Artun Saday, İlker Demirel, Yiğit Yıldırım, Cem Tekin, "Federated Multi-Armed Bandits Under Byzantine Attacks".
November 2024: Our paper has been published in IEEE Transactions on Information Theory: Eray Can Elumar, Cem Tekin, Osman Yağan, "Multi-armed Bandits with Costly Probes".
Recent Research Areas
Combinatorial Optimization in Unknown Environments
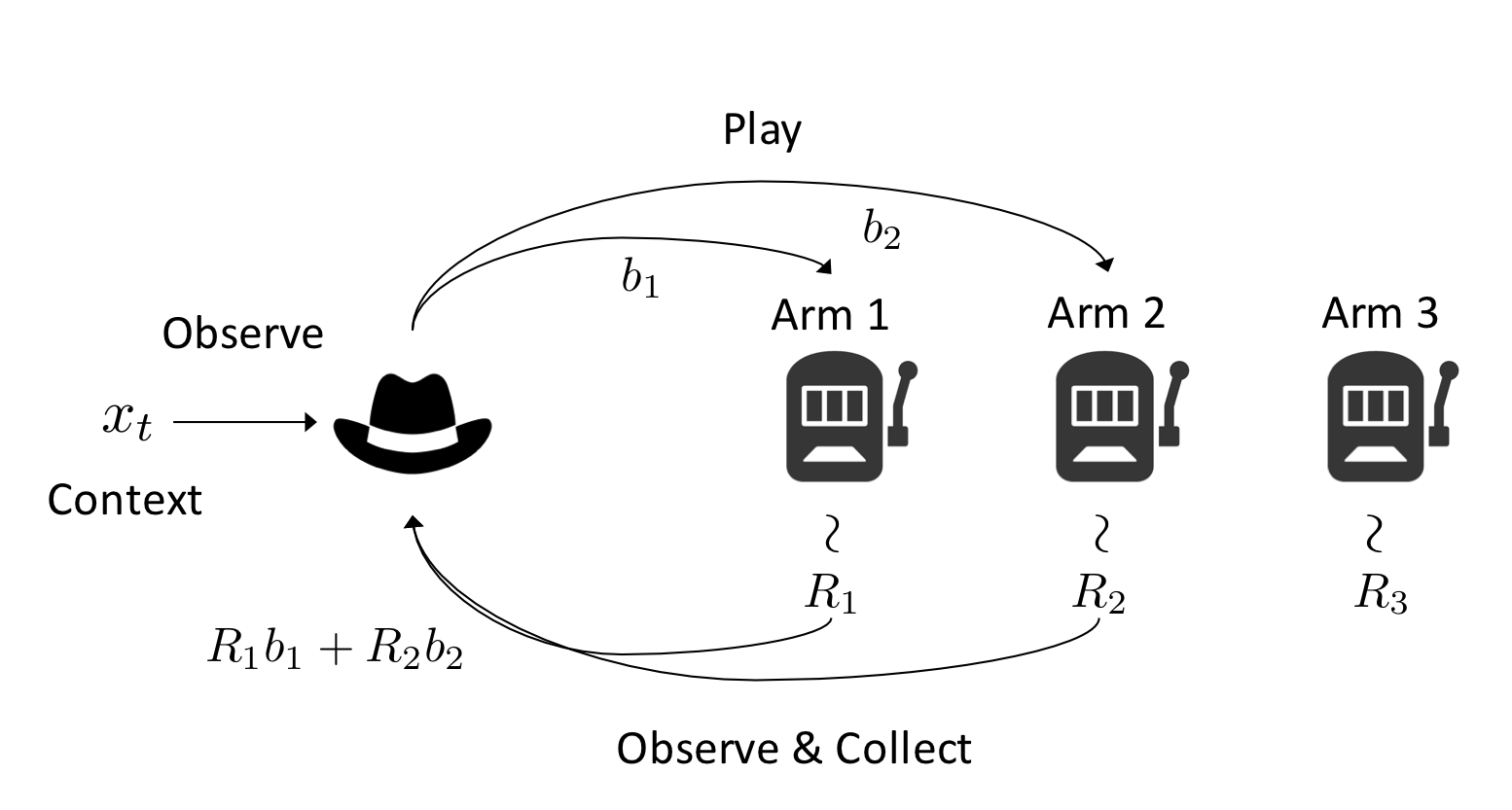
How should an advertiser promote its products on a social network to reach many users with a limited budget? How should a search engine suggest a ranked list of items to its users to maximize the click-through rate? How should a base station allocate its users to channels to maximize the system throughput? How should a mobile crowdsourcing platform dynamically assign available tasks to its workers to maximize performance? How can we identify the most reliable paths from source to destination under probabilistic link failures? All of these problems require optimizing decisions among a vast set of alternatives. When the probabilistic description of the environment is fully specified, these problems and many others are solved using computationally efficient exact or approximation algorithms. In this line of research, we focus on a much more difficult and realistic problem: How should we learn the optimal decisions in these complex problems via repeated interaction with the environment when the probabilistic description of the environment is unknown or only partially known?
It is natural to assume that the environment is unknown in many real-world applications. For instance, the advertiser may not know with what probability user i will influence its neighbor j in the social network or the search engine may not know with what probability user i will click the item shown on position j beforehand. Moreover, decisions need to be made sequentially over time. For instance, the recommender system should show each arriving user a new list of items. The base station should reallocate network resources when the channel conditions change, or the users leave/enter the system. Future decisions of the learner must be guided based on what it has observed thus far, i.e., the trajectory of actions, observations and rewards generated by the learner's past decisions. Importantly, both the cumulative reward of the learner and what it has learned so far also depend on this trajectory. Therefore, the learner needs to balance how much it earns (exploiting the actions it believes to be the best) and how much it learns (exploring actions it does not know much about) to maximize its long-term performance. We solve the formidable task of combinatorial optimization in unknown environments by modeling it as a combinatorial multi-armed bandit.
Related Publications
| S. Elahi, B. Atalar, S. Ogut, C. Tekin, "Contextual combinatorial multi-output GP bandits with group constraints", Transactions on Machine Learning Research, July 2023. | |
| A. Nika, S. Elahi, C. Tekin, "Online context-aware task assignment in mobile crowdsourcing via adaptive discretization", IEEE Transactions on Network Science and Engineering, 10(1): 305-320, January-February 2023. | |
| M. A. Qureshi, A. Nika, C. Tekin, "Multi-user small base station association via contextual combinatorial volatile bandits", IEEE Transactions on Communications, 69(6): 3726-3740, June 2021. | I. Demirel, C. Tekin, "Combinatorial Gaussian process bandits with probabilistically triggered arms", in Proc. 24th International Conference on Artificial Intelligence and Statistics (AISTATS), April 2021. | A. Nika, S. Elahi, C. Tekin, "Contextual combinatorial volatile multi-armed bandit with adaptive discretization", in Proc. 23rd International Conference on Artificial Intelligence and Statistics (AISTATS), August 2020. |
| A. Huyuk, C. Tekin, "Thompson sampling for combinatorial network optimization in unknown environments", IEEE/ACM Transactions on Networking, 28(6): 2836-2849, December 2020. | |
| O. Saritac, A. Karakurt, C. Tekin " Online contextual influence maximization with costly observations", IEEE Transactions on Signal and Information Processing over Networks, 5(2): 273-289, June 2019. | A. Huyuk, C. Tekin, " Analysis of Thompson sampling for combinatorial multi-armed bandit with probabilistically triggered arms", in Proc. 22nd International Conference on Artificial Intelligence and Statistics (AISTATS), April 2019. | A. O. Saritac, C. Tekin, "Combinatorial multi-armed bandit problem with probabilistically triggered arms: A case with bounded regret", in Proc. IEEE GlobalSIP, November 2017. | A. O. Saritac, A. Karakurt, C. Tekin, "Online contextual influence maximization in social networks", in Proc. 54th Allerton Conference, September 2016. |
Multi-Objective Multi-Armed Bandit
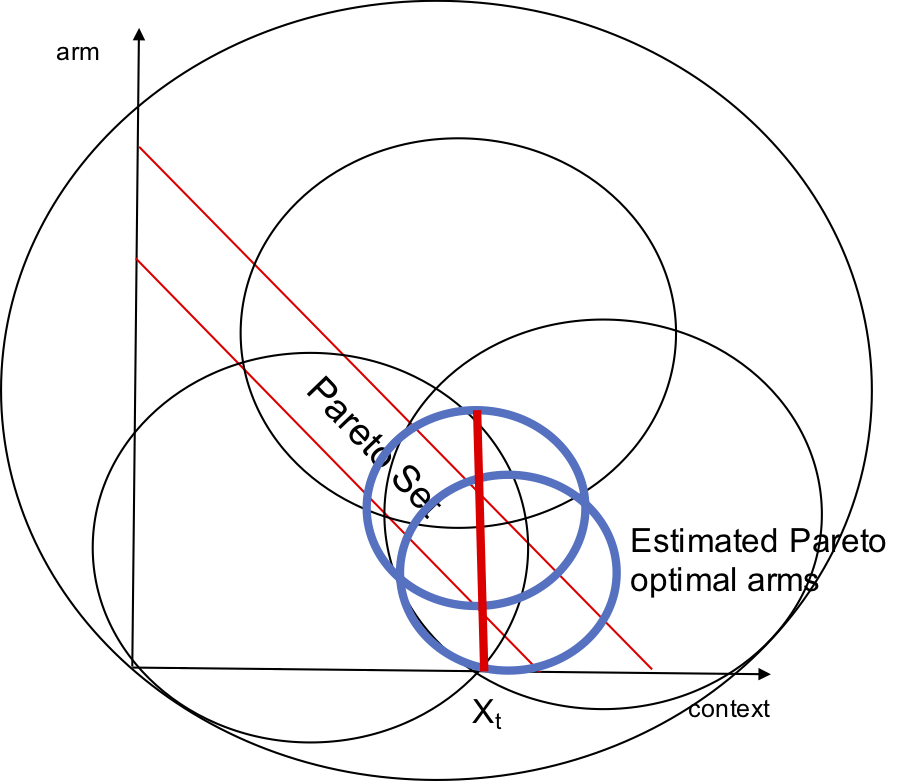
The multi-armed bandit (MAB) is extensively used to model sequential decision-making problems with uncertain rewards. While many real-world applications, ranging from cognitive radio networks to recommender systems to medical diagnosis, require intelligent decision-making mechanisms that learn from the past, most of these applications involve multiple and possibly conflicting objectives, which does not fit into the classical MAB model. For instance, these objectives include throughput and reliability in a cognitive radio network, semantic match and job-seeking intent in a talent recommender system, and sensitivity and specificity in medical diagnosis. Motivated by the applications and the challenges above, in this line of research we develop new MAB models that address the learning challenges that arise from multiple and possibly conflicting objectives.
Related Publications
| A. Huyuk, C. Tekin, "Multi-objective multi-armed bandit with lexicographically ordered and satisficing objectives", Machine Learning, 110: 1233-1266, May 2021. | |
| C. Tekin, E. Turgay " Multi-objective contextual multi-armed bandit problem with a dominant objective", IEEE Transactions on Signal Processing, 66(14): 3799-3813, July, 2018. | E. Turgay, D. Oner, C. Tekin, " Multi-objective contextual bandit problem with similarity information", in Proc. 21st International Conference on Artificial Intelligence and Statistics (AISTATS), April 2018. | C. Tekin, E. Turgay, "Multi-objective contextual bandits with a dominant objective", in Proc. IEEE MLSP, September 2017. |
Beyond Multi-Objective: Vector Optimization With Bandit Feedback
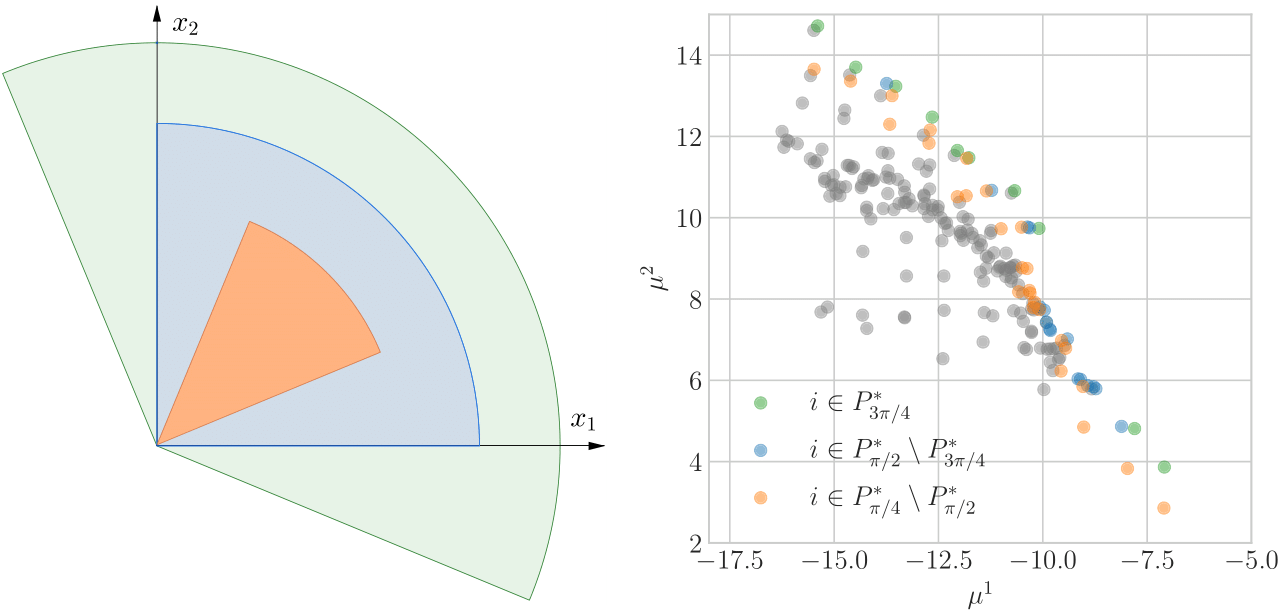
Many complex scientific and engineering problems, including vaccine development and deep neural architecture search, require identifying optimal designs that satisfy specific performance criteria from a design set that includes many alternative designs via sequential experimentation. This problem has been mainly investigated in the literature when there is a single performance objective to be optimized. Due to their complex nature, many real-world applications of active learning require the optimization of multiple objectives. Moreover, the experimenter can have complex tradeoffs among multiple objectives beyond the standard component-wise order used in multi-objective optimization. The goal is to identify Pareto optimal designs that are not dominated by other designs. We open a new frontier in this direction by incorporating arbitrary preferences encoded by polyhedral ordering cones into the sequential decision-making framework.
It is very difficult for domain experts to design optimal sequential experiments for problems that involve large design sets, multiple performance objectives intricately tied with each other, and restrictions on observations of design performances, such as partial and noisy observations. Our goal is to design active learning algorithms that are mathematically rigorously founded, provably efficient, and scalable for learning problems in which the Pareto set of designs (according to a given cone) needs to be found with sequential experimentation by using the minimum amount of resources. The algorithms developed in this research will enable experts in various disciplines, ranging from biology to data science, to identify optimal designs with minimum experimentation.
Related Publications
| E. M. Karagozlu, Y. C. Yıldırım, C. Ararat, C. Tekin, "Learning the Pareto set under incomplete preferences: Pure exploration in vector bandits", in Proc. 27th International Conference on Artificial Intelligence and Statistics (AISTATS), May 2024. | |
| C. Ararat, C. Tekin, "Vector optimization with stochastic bandit feedback", in Proc. 26th International Conference on Artificial Intelligence and Statistics (AISTATS), April 2023. |
Bayesian Satisficing
Machine learning has started playing an existential role in solving sequential experimental design (SED) problems that pave the path toward new scientific discoveries and breakthrough engineering products. Searching for an efficient design requires navigating through complex search spaces via sequential experiments. After several decades of tremendous research effort, Bayesian optimization (BO) is shown to be a promising tool for real-world SED problems. However, the search for the optimal is often futile due to the immense complexity of the objective function and design space; and distribution mismatches that are prevalent in real-world problems. Therefore, BO falls short of addressing key performance objectives: sample efficient, accurate, and robust identification of efficient designs. Our research aims to open a new frontier by formalizing the search for an efficient design from the lens of satisficing, an alternative model for rational decision-making pioneered by Herbert Simon, which can be described as achieving a satisfactory target utility under uncertainty. We aim to develop novel acquisition strategies that will achieve significant improvement in performance objectives compared to the best BO methods. This requires establishing new acquisition functions, and new techniques to deal with radical uncertainty and distribution shifts.
Related Publications
| A. Saday, Y. C. Yıldırım, C. Tekin, "Robust Bayesian satisficing", in Proc. 37th Conference on Neural Information Processing Systems (NeurIPS), December 2023. |
People

Cem Tekin
Cem is an Associate Professor in the Department of Electrical and Electronics Engineering and Head of the Cognitive Systems, Bandits, and Optimization Research Group (CYBORG) at Bilkent University.
He received his PhD degree in Electrical Engineering: Systems from the University of Michigan, Ann Arbor, in 2013 (advisor: Mingyan Liu). He also received his MS in Mathematics and MSE in Electrical Engineering: Systems from the University of Michigan in 2011 and 2010, respectively. Before attending the University of Michigan, he received his BS in Electrical and Electronics Engineering (valedictorian) from METU in 2008. From February 2013 to January 2015, he was a postdoctoral scholar in the Electrical Engineering Department, UCLA (advisor: Mihaela van der Schaar). He received the Fred W. Ellersick Award for the best paper in MILCOM 2009, the Science Academy Association of Türkiye Distinguished Young Scientist (BAGEP) Award in 2019, Parlar Foundation Research Incentive Award in 2019, IEEE Türkiye Chapter Research Incentive Award in 2020, Bilkent University Distinguished Teaching Award in 2023, TÜBA-GEBİP Award in 2023, and TÜBİTAK Incentive Award in 2024. He is a Senior Member of IEEE.
Cem has authored or co-authored over 75 research papers, 5 book chapters, and a research monograph. He is currently serving as an Associate Editor for IEEE Transactions on Networking. He has served as a reviewer for numerous journals, including JMLR, Machine Learning, IEEE Transactions on Information Theory, IEEE Transactions on Automatic Control, IEEE/ACM Transactions on Networking, IEEE Transactions on Signal Processing, IEEE Transactions on Wireless Communications, IEEE JSTSP and IEEE JSAC.
He has served as an area chair for AISTATS-23, AISTATS-24, AISTATS-25, and AISTATS-26. He has been actively reviewing for top ML conferences, including NeurIPS-25, ICML-25, NeurIPS-24, ICML-24, ICLR-24, NeurIPS-23, ICML-23, NeurIPS-22, ICML-22, ICLR-22, AISTATS-22, NeurIPS-21, ICML-21, AISTATS-21, NeurIPS-20, ICML-20.
Cem's research interests include bandit problems, reinforcement learning, artificial intelligence for medicine, multi-agent systems, stream mining, influence maximization and cognitive communications.
Current Graduate Students

Ali Ünlü
Ali is a PhD student at the Department of Electrical and Electronics Engineering at Bilkent University. Coming from a CS background, he is primarily interested in Deep Learning, Robust Optimization, and Bayesian Inference.

Artun Saday
Artun is a PhD student in the Department of Electrical and Electronics Engineering at Bilkent University. His research areas are robust decision-making under uncertainty, Bayesian Optimization, and Gaussian processes. Beyond his primary research, Artun is also interested in complex systems and philosophy of mind.

Enes Ağırman
Enes is an MS student in the Department of Electrical and Electronics Engineering at Bilkent University. His research interests include statistical learning, robust optimization, multi-armed bandits, reinforcement learning, and machine learning for healthcare.

Muhammad Usman Shahid
Usman is a PhD student at the Department of Electrical and Electronics Engineering at Bilkent University. His research interests include robust satisficing bandits for cognitive communications, Bayesian optimization, and Gaussian processes.

Umut Eren Aktürk
Umut is an MS student in the Department of Electrical and Electronics Engineering at Bilkent University. His current research is aimed at contextual combinatorial bandits.

Yaşar Cahit Yıldırım
Cahit received his MS from Bilkent EEE in 2025. His research is aimed at stochastic optimization of complex, unknown systems.
Recent Alumni

İlter Onat Korkmaz [Moved to Texas A&M University for PhD]
İlter received his MS from the Department of Electrical and Electronics Engineering at Bilkent University in 2025. His research interests are multi-objective optimization, Bayesian optimization, Gaussian processes, and vector optimization.

Yiğit Narter [Moved to University of Michigan EECS for PhD]
Yiğit graduated from the Department of Electrical and Electronics Engineering at Bilkent University with a 3.99 GPA as the valedictorian in 2025. Yiğit’s research interests include applied probability and machine learning for healthcare.

Efe Mert Karagözlü [Moved to CMU CS for PhD]
Efe Mert graduated from the Department of Electrical and Electronics Engineering at Bilkent University with a 4.00 GPA as the valedictorian in 2024. His research interest includes pure exploration problems and vector optimization.

İlker Demirel [Moved to MIT EECS for PhD]
Ilker is interested in statistical machine learning and sequential decision-making under uncertainty with applications to healthcare, distributed learning, and optimization.

Kerem Bozgan [Moved to Virginia Tech for PhD]
Kerem's research interests include multi-objective and robust Bayesian optimization.

Baran Atalar [Moved to CMU ECE for PhD]
Baran is interested in reinforcement learning, multi-armed bandit problems, online learning and machine learning in general. He is currently working on contextual combinatorial volatile bandits with thresholds, and mmWave beam selection problem for vehicular communications.

Batu Arda Düzgün [Moved to ETH for Master in Electrical Engineering and Information Technology]
Batu works on bandit algorithms and PAC best arm identification.

Sepehr Elahi [Moved to EPFL for PhD]
Sepehr has authored papers on online decision making, contextual bandits, Gaussian processes, multi-objective optimization, and their applications to crowdsourcing/sensing, content recommendation, and item recommendation. Besides the previously mentioned, he is also interested in federated learning, Bayesian learning, and in general statistical machine learning.

Sevda Ögüt [Moved to EPFL for PhD]
Sevda's research interests include multi-armed bandits, especially in contextual, combinatorial and volatile settings, Gaussian processes, thresholding and applications of these to content caching and mmWave communications.

Mehmet Ufuk Özdemir [Moved to UCLA ECE for PhD]
Ufuk's research interests include safe bandit algorithms and vector optimization with stochastic bandit feedback.
Alumni
Ahmet Alparslan Çelik [Former MS student]
Andi Nika [Former MS student, now PhD student at Max Planck Institute for Software Systems]
Alireza Javanmardi [Former MS student, now PhD student at Ludwig Maximilian University of Munich]
Muhammad Anjum Qureshi [Former PhD student, now Senior Research Officer at Ministry of Science and Technology, Pakistan]
Alihan Hüyük [Former undergraduate student, now Postdoctoral Fellow at Harvard University]
Doruk Öner [Former undergraduate student, now Assistant Professor at Bilkent University]
Anıl Ömer Sarıtaç [Former MS student, now Assistant Professor of Operations Management at Singapore Management University]
Nima Akbarzadeh [Former MS student, now Postdoctoral Fellow at MILA and HEC Montreal]
Cem Bulucu [Former MS student, now Senior Artificial Intelligence Engineer at Loop Games]
Ümitcan Şahin [Former MS student, now Research Engineer at ASELSAN Research Center]
Eralp Turğay [Former MS student, now AI Research Team Lead at Lyrebird Studio]
Kubilay Ekşioğlu [Former MS student]
Publications
Papers in top AI&ML conferences
| [T15] | A. Saday, Y. C. Yıldırım, C. Tekin, "Robust satisficing Gaussian process bandits under adversarial attacks", accepted to NeurIPS 2025. |
| [T14] | E. C. Elumar, C. Tekin, O. Yagan, "Cost-aware LLM-based online dataset annotation", accepted to NeurIPS 2025 as Spotlight Paper (13% of accepted papers). |
| [T13] | Y. Narter, A. Hüyük, M. van der Schaar, C. Tekin, "Unified screening for multiple diseases", in Proc. 42nd International Conference on Machine Learning (ICML), July 2025. |
| [T12] | E. M. Karagozlu, Y. C. Yıldırım, C. Ararat, C. Tekin, "Learning the Pareto set under incomplete preferences: Pure exploration in vector bandits", in Proc. 27th International Conference on Artificial Intelligence and Statistics (AISTATS), May 2024. |
| [T11] | A. Saday, Y. C. Yıldırım, C. Tekin, "Robust Bayesian satisficing", in Proc. 37th Conference on Neural Information Processing Systems (NeurIPS), December 2023. |
| [T10] | C. Ararat, C. Tekin, "Vector optimization with stochastic bandit feedback", in Proc. 26th International Conference on Artificial Intelligence and Statistics (AISTATS), April 2023. |
| [T9] | I. Demirel, A. A. Celik, C. Tekin, "ESCADA: Efficient safety and context aware dose allocation for precision medicine", in Proc. 36th Conference on Neural Information Processing Systems (NeurIPS), December 2022. | [T8] | A. Huyuk, D. Jarret, C. Tekin, M. van der Schaar, "Explaining by imitating: Understanding decisions by interpretable policy learning", in Proc. 9th International Conference on Learning Representations (ICLR), May 2021. | [T7] | I. Demirel, C. Tekin, "Combinatorial Gaussian process bandits with probabilistically triggered arms", in Proc. 24th International Conference on Artificial Intelligence and Statistics (AISTATS), April 2021. | [T6] | A. Nika, S. Elahi, C. Tekin, "Contextual combinatorial volatile multi-armed bandit with adaptive discretization", in Proc. 23rd International Conference on Artificial Intelligence and Statistics (AISTATS), August 2020. | [T5] | X. Zhang, M. M. Khalili, C. Tekin, M. Liu, "Group retention when using machine learning in sequential decision making: The interplay between user dynamics and fairness", in Proc. 33rd Conference on Neural Information Processing Systems (NeurIPS), December 2019. | [T4] | A. Huyuk, C. Tekin, "Analysis of Thompson sampling for combinatorial multi-armed bandit with probabilistically triggered arms", in Proc. 22nd International Conference on Artificial Intelligence and Statistics (AISTATS), April 2019. | [T3] | E. Turgay, D. Oner, C. Tekin, "Multi-objective contextual bandit problem with similarity information", in Proc. 21st International Conference on Artificial Intelligence and Statistics (AISTATS), April 2018. | [T2] | O. Atan, C. Tekin, M. van der Schaar, " Global multi-armed bandits with Hölder continuity", in Proc. 18th International Conference on Artificial Intelligence and Statistics (AISTATS), April 2015. | [T1] | C. Tekin, M. van der Schaar, " Discovering, learning and exploiting relevance", in Proc. 28th Annual Conference on Neural Information Processing Systems (NeurIPS), December 2014. |
Preprints
| [I3] | Y. C. Yıldırım, E. M. Karagözlü, İ. O. Korkmaz, Ç. Ararat, C. Tekin, "VOPy: A framework for black-box vector optimization". |
| [I2] | İ. O. Korkmaz, Y. C. Yıldırım, Ç. Ararat, C. Tekin, "Vector optimization with Gaussian process bandits". |
Monograph
| [M1] | C. Tekin, M. Liu, "Online learning methods in networking", Foundations and Trends in Networking, January 2015. |
Book chapters
| [B5] | R. Ducasse, C. Tekin, M. van der Schaar, "Finding it now: Networked classifiers in real-time stream mining systems", in Handbook of Signal Processing Systems, Springer, 2018. |
| [B4] | C. Tekin, S. Zhang, J. Xu, M. van der Schaar, "Multi-agent systems: Learning, strategic behavior, cooperation, and network formation", in Cooperative and Graph Signal Processing, Elsevier, 2018. |
| [B3] | C. Tekin, M. van der Schaar, "Actionable intelligence and online learning for semantic computing", in Encyclopedia with Semantic Computing and Robotic Intelligence, 01, 1630011, 2017. |
| [B2] | S. S. Bhattacharyya, M. van der Schaar, O. Atan, C. Tekin, K. Sudusinghe, "Data-driven stream mining systems for computer vision", in Advances in Embedded Computer Vision, Springer, November 2014. |
| [B1] | C. Tekin, M. Liu, "Performance and convergence of multiuser online learning and its application in dynamic spectrum sharing", in Mechanisms and Games for Dynamic Spectrum Allocation, Cambridge University Press, February 2014. |
Journal papers
| [J39] | A. Nika, S. Elahi, C. Tekin, "Contextual combinatorial bandits with changing action sets via Gaussian processes", Transactions on Machine Learning Research, October 2025. |
| [J38] | A. Nika, S. Elahi, C. Ararat, C. Tekin, "Beyond grids: Multi-objective Bayesian optimization with adaptive discretization", Transactions on Machine Learning Research, August 2025. |
| [J37] | A. Saday, I. Demirel, Y Yildirim, C. Tekin, "Federated multi-armed bandits under Byzantine attacks", IEEE Transactions on Artificial Intelligence, 6(6): 1488 - 1501, June 2025. |
| [J36] | E. C. Elumar, C. Tekin, O. Yagan, "Multi-armed bandits with costly probes", IEEE Transactions on Information Theory, 71(1): 618-643, January 2025. |
| [J35] | M. Abroshan, K. H. Yip, C. Tekin, M. van der Schaar, "Conservative policy construction using variational autoencoders for logged data with missing values", IEEE Transactions on Neural Networks and Learning Systems, 34(9), September 2023. |
| [J34] | S. Elahi, B. Atalar, S. Ogut, C. Tekin, "Contextual combinatorial multi-output GP bandits with group constraints", Transactions on Machine Learning Research, July 2023. |
| [J33] | A. Nika, S. Elahi, C. Tekin, "Online context-aware task assignment in mobile crowdsourcing via adaptive discretization", IEEE Transactions on Network Science and Engineering, 10(1): 305-320, January-February 2023. |
| [J32] | A. Javanmardi, M. A. Qureshi, C. Tekin, "Decentralized dynamic rate and channel selection over a shared spectrum", IEEE Transactions on Communications, 69(6): 3787-3801, June 2021. |
| [J31] | M. A. Qureshi, A. Nika, C. Tekin, "Multi-user small base station association via contextual combinatorial volatile bandits", IEEE Transactions on Communications, 69(6): 3726-3740, June 2021. |
| [J30] | A. Huyuk, C. Tekin, "Multi-objective multi-armed bandit with lexicographically ordered and satisficing objectives", Machine Learning, 110: 1233-1266, May 2021. |
| [J29] | E. Turgay, C. Bulucu, C. Tekin, "Exploiting relevance for online decision-making in high-dimensions", IEEE Transactions on Signal Processing, 69: 1438-1451, December 2020. |
| [J28] | C. Tekin, S. Elahi, M. van der Schaar, "Feedback adaptive learning for medical and educational application recommendation", to appear in IEEE Transactions on Services Computing, 2020. |
| [J27] | A. Huyuk, C. Tekin, "Thompson sampling for combinatorial network optimization in unknown environments", IEEE/ACM Transactions on Networking, 28(6): 2836-2849, December 2020. |
| [J26] | M. A. Qureshi, C. Tekin, "Rate and channel adaptation in cognitive radio networks under time-varying constraints", IEEE Communications Letters, 24(12): 2979-2983, December 2020. |
| [J25] | M. A. Qureshi, C. Tekin, "Fast learning for dynamic resource allocation in AI-enabled radio networks", IEEE Transactions on Cognitive Communications and Networking, 6(1): 95-110, March 2020. |
| [J24] | O. Saritac, A. Karakurt, C. Tekin, "Online contextual influence maximization with costly observations", IEEE Transactions on Signal and Information Processing over Networks, 5(2): 273-289, June 2019. |
| [J23] | C. Tekin, "The biobjective multiarmed bandit: Learning approximate lexicographic optimal allocations", Turkish Journal of Electrical Engineering and Computer Sciences, 27(2): 1065-1080, March 2019. |
| [J22] | N. Akbarzadeh, C. Tekin, M. van der Schaar, "Online learning in limit order book trade execution", IEEE Transactions on Signal Processing, 66(17): 4626-4641, September, 2018. |
| [J21] | H. S. Lee, C. Tekin, M. van der Schaar, J. W. Lee, "Adaptive contextual learning for unit commitment in microgrids with renewable energy sources", IEEE Journal of Selected Topics in Signal Processing, 12(4): 688-702, August, 2018. |
| [J20] | C. Tekin, E. Turgay, "Multi-objective contextual multi-armed bandit problem with a dominant objective", IEEE Transactions on Signal Processing, 66(14): 3799-3813, July, 2018. |
| [J19] | S. Muller, C. Tekin, M. van der Schaar, A. Klein, "Context-aware hierarchical online learning for performance maximization in mobile crowdsourcing", IEEE/ACM Transactions on Networking, 26(3): 1334-1347, June, 2018. |
| [J18] | O. Atan, C. Tekin, M. van der Schaar, "Global bandits", IEEE Transactions on Neural Networks and Learning Systems, 29(12): 5798-5811, December 2018. |
| [J17] | R. B. Hellman, C. Tekin, M. van der Schaar, V. J. Santos, "Functional contour-following via haptic perception and reinforcement learning", IEEE Transactions on Haptics, 11(1): 61-72, January-March, 2018. |
| [J16] | C. Shen, R. Zhou, C. Tekin, M. van der Schaar, "Generalized global bandit and its application in cellular coverage optimization", IEEE Journal of Selected Topics in Signal Processing, 12(1): 218-232, January, 2018. |
| [J15] | C. Tekin J. Yoon, M. van der Schaar, "Adaptive ensemble learning with confidence bounds", IEEE Transactions on Signal Processing, 65(4): 888-903, February 2017. |
| [J14] | C. Shen, C. Tekin and M. van der Schaar, "A non-stochastic learning approach to energy efficient mobility management", IEEE Journal on Selected Areas in Communications (JSAC), 34(12): 3854-3868, December 2016. |
| [J13] | K. Kanoun, C. Tekin, D. Atienza, M. van der Schaar, "Big-data streaming applications scheduling based on staged multi-armed bandits", IEEE Transactions on Computers, 65(12): 3591-3605, December 2016. |
| [J12] | S.D. Amuru, C. Tekin, M. van der Schaar, R. Buehrer, "Jamming bandits - A novel learning method for optimal jamming", IEEE Transactions on Wireless Communications, 15(4):2792-2808, April 2016. |
| [J11] | C. Tekin, M. van der Schaar, "Distributed online learning via cooperative contextual bandits", IEEE Transactions on Signal Processing, 63(14):3740–3754, July 2015. |
| [J10] | C. Tekin, M. van der Schaar, "Active learning in context-driven stream mining with an application to image mining", IEEE Transactions on Image Processing, 24(11): 3666-3679, June 2015. |
| [J9] | C. Tekin, M. van der Schaar, "RELEAF: An algorithm for learning and exploiting relevance", IEEE Journal of Selected Topics in Signal Processing (JSTSP), 9(4):716–727, June 2015. |
| [J8] | C. Tekin O. Atan, M. van der Schaar, "Discover the expert: Context-adaptive expert selection for medical diagnosis", IEEE Transactions on Emerging Topics in Computing, 3(2):220–234, June 2015. |
| [J7] | J. Xu, C. Tekin, S. Zhang, M. van der Schaar, "Distributed multi-agent online learning based on global feedback", IEEE Transactions on Signal Processing, 63(9):2225–2238, May 2015. |
| [J6] | C. Tekin, M. van der Schaar, "Contextual online learning for multimedia content aggregation", IEEE Transactions on Multimedia, 17(4):549-561, April 2015. |
| [J5] | O. Atan, Y. Andreopoulos, C. Tekin, M. van der Schaar, "Bandit framework for systematic learning in wireless video-based face recognition", IEEE Journal of Selected Topics in Signal Processing (JSTSP) , 9(1):180–194, February 2015. |
| [J4] | L. Song, C. Tekin, M. van der Schaar, "Online learning in large-scale contextual recommender systems", IEEE Transactions on Services Computing, 9(3): 433-445, 2016. |
| [J3] | C. Tekin, S. Zhang, M. van der Schaar, "Distributed online learning in social recommender systems", IEEE Journal of Special Topics in Signal Processing (JSTSP), 8(4): 638-652, August 2014. |
| [J2] | C. Tekin, M. Liu, R. Southwell, J. Huang, S. H. A. Ahmad, "Atomic congestion games on graphs and their applications in networking", IEEE/ACM Transactions on Networking (ToN), 20(5): 1541-1552, October 2012. |
| [J1] | C. Tekin M. Liu, "Online learning of rested and restless bandits", IEEE Transactions on Information Theory (IT), 58(8): 5558-5611, August 2012. |
Papers in conference proceedings
| [C41] | A. Saday, Y. C. Yıldırım, C. Tekin, "Robust satisficing Gaussian process bandits under adversarial attacks", accepted to NeurIPS 2025. |
| [C40] | E. C. Elumar, C. Tekin, O. Yagan, "Cost-aware LLM-based online dataset annotation", accepted to NeurIPS 2025 as Spotlight Paper (13% of accepted papers). |
| [C39] | Y. Narter, A. Hüyük, M. van der Schaar, C. Tekin, "Unified screening for multiple diseases", in Proc. 42nd International Conference on Machine Learning (ICML), July 2025. |
| [C38] | E. C. Elumar, C. Tekin, O. Yagan, "Multi-armed bandits with probing", in Proc. 2024 IEEE International Symposium on Information Theory (ISIT), July 2024. |
| [C37] | E. M. Karagozlu, Y. C. Yıldırım, C. Ararat, C. Tekin, "Learning the Pareto set under incomplete preferences: Pure exploration in vector bandits", in Proc. 27th International Conference on Artificial Intelligence and Statistics (AISTATS), May 2024. |
| [C36] | A. Saday, Y. C. Yıldırım, C. Tekin, "Robust Bayesian satisficing", in Proc. 37th Conference on Neural Information Processing Systems (NeurIPS), December 2023. |
| [C35] | C. Ararat, C. Tekin, "Vector optimization with stochastic bandit feedback", in Proc. 26th International Conference on Artificial Intelligence and Statistics (AISTATS), April 2023. |
| [C34] | I. Demirel, A. A. Celik, C. Tekin, "ESCADA: Efficient safety and context aware dose allocation for precision medicine", in Proc. 36th Conference on Neural Information Processing Systems (NeurIPS), December 2022. | [C33] | A. Huyuk, D. Jarret, C. Tekin, M. van der Schaar, "Explaining by imitating: Understanding decisions by interpretable policy learning", in Proc. 9th International Conference on Learning Representations (ICLR), May 2021. | [C32] | I. Demirel, C. Tekin, "Combinatorial Gaussian process bandits with probabilistically triggered arms", in Proc. 24th International Conference on Artificial Intelligence and Statistics (AISTATS), April 2021. | [C31] | A. Nika, S. Elahi, C. Tekin, "Contextual combinatorial volatile multi-armed bandit with adaptive discretization", in Proc. 23rd International Conference on Artificial Intelligence and Statistics (AISTATS), August 2020. | [C30] | M. A. Qureshi, C. Tekin, "Online Bayesian learning for rate selection in millimeter wave cognitive radio networks", Proc. 2020 IEEE Conference on Computer Communications (INFOCOM), July 2020. | [C29] | X. Zhang, M. M. Khalili, C. Tekin, M. Liu, "Group retention when using machine learning in sequential decision making: The interplay between user dynamics and fairness", in Proc. 33rd Conference on Neural Information Processing Systems (NeurIPS), December 2019. | [C28] | A. Huyuk, C. Tekin, "Analysis of Thompson sampling for combinatorial multi-armed bandit with probabilistically triggered arms", in Proc. 22nd International Conference on Artificial Intelligence and Statistics (AISTATS), April 2019. | [C27] | E. Turgay, D. Oner, C. Tekin, "Multi-objective contextual bandit problem with similarity information", in Proc. 21st International Conference on Artificial Intelligence and Statistics (AISTATS), April 2018. | [C26] | A. O. Saritac, C. Tekin, "Combinatorial multi-armed bandit problem with probabilistically triggered arms: A case with bounded regret", in Proc. IEEE GlobalSIP, November 2017. | [C25] | N. Akbarzadeh, C. Tekin, M. van der Schaar, "Online learning in limit order book trade execution", in Proc. IEEE GlobalSIP, November 2017. | [C24] | C. Tekin, E. Turgay, "Multi-objective contextual bandits with a dominant objective", in Proc. IEEE MLSP, September 2017. | [C23] | H. Lee, C. Tekin, M. van der Schaar, J. Lee, "Contextual learning for unit commitment with renewable energy sources", in Proc. IEEE GlobalSIP , December 2016. | [C22] | A. O. Saritac, A. Karakurt, C. Tekin, "Online contextual influence maximization in social networks", in Proc. 54th Allerton Conference, September 2016, Monticello, Illinois. | [C21] | N. Akbarzadeh, C. Tekin, "Gambler's ruin bandit problem", in Proc. 54th Allerton Conference, September 2016, Monticello, Illinois. | [C20] | C. Tekin, J. Yoon, M. van der Schaar, "Adaptive ensemble learning with confidence bounds for personalized diagnosis", in AAAI Workshop on Expanding the Boundaries of Health Informatics using AI (HIAI'16): Making Proactive, Personalized, and Participatory Medicine A Reality, February, 2016. | [C19] | O. Atan, C. Tekin, M. van der Schaar, " Global Multi-armed Bandits with Hölder Continuity", in Proc. 18th International Conference on Artificial Intelligence and Statistics (AISTATS), April 2015. | [C18] | C. Tekin, Jonas Braun, M. van der Schaar, "eTutor: Online learning for personalized education", in Proc. 40th IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), April 2015. | [C17] | Onur Atan, William Hsu, C. Tekin, M. van der Schaar, "A data-driven approach for matching clinical expertise to individual cases", in Proc. 40th IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), April 2015. | [C16] | S.D. Amuru, C. Tekin, M. van der Schaar, R. Buehrer, "A systematic learning method for optimal jamming", in Proc. IEEE International Conference on Communications (ICC), May 2015. | [C15] | C. Tekin, M. van der Schaar, " Discovering, learning and exploiting relevance", in Proc. 28th Annual Conference on Neural Information Processing Systems (NIPS), December 2014, Montreal, Canada. | [C14] | C. Tekin, M. van der Schaar, "An experts learning approach to mobile service offloading", in Proc. 52nd Allerton Conference, October 2014, Monticello, Illinois. | [C13] | C. Tekin , L. Canzian, M. van der Schaar, "Context adaptive Big Data stream mining", in Proc. 52nd Allerton Conference, October 2014, Monticello, Illinois. |
| [C12] | O. Atan, Y. Andreopoulos, C. Tekin, M. van der Schaar, "Bandit framework for systematic learning in wireless video-based face recognition", in Proc. 39th IEEE International Conference on Acoustics, Speech, and Signal Processing (ICASSP), 2014. |
| [C11] | L. Song, C. Tekin, M. van der Schaar, " Clustering based online learning in recommender systems: a bandit approach", in Proc. 39th IEEE International Conference on Acoustics, Speech, and Signal Processing (ICASSP), 2014. |
| [C10] | J. Xu, C. Tekin, M. van der Schaar, " Learning optimal classifier chains for real-time big data mining", in Proc. 51st Allerton Conference, October 2013, Monticello, Illinois. |
| [C9] | C. Tekin, M. van der Schaar, " Distributed online Big Data classification using context information", in Proc. 51st Allerton Conference, October 2013, Monticello, Illinois. |
| [C8] | C. Tekin, M. Liu, " Online learning in decentralized multi-user spectrum access with synchronized explorations", in Proc. IEEE Military Communications Conference (MILCOM), October 2012. |
| [C7] | C. Tekin, M. Liu, " Approximately optimal adaptive learning in opportunistic spectrum access", in Proc. 31st IEEE International Conference on Computer Communications (INFOCOM), March 2012, Orlando, Florida. |
| [C6] | C. Tekin, M. Liu, " Adaptive learning of uncontrolled restless bandits with logarithmic regret", in Proc. 49th Allerton Conference, September 2011, Monticello, Illinois. |
| [C5] | C. Tekin, M. Liu, " Performance and convergence of multi-user online learning", in Proc. 2nd International ICST Conference on Game Theory for Networks (GAMENETS), April 2011, Shanghai, China. |
| [C4] | C. Tekin, M. Liu, " Online learning in opportunistic spectrum access: a restless bandit approach", in Proc. 30th IEEE International Conference on Computer Communications (INFOCOM), April 2011, Shanghai, China. |
| [C3] | C. Tekin, M. Liu, " Online algorithms for the multi-armed bandit problem with Markovian rewards", in Proc. 48th Allerton Conference, September 2010, Monticello, Illinois. |
| [C2] | S. Hong, E. Like, Z. Wu, C. Tekin, " Multi-user signal classification via spectral correlation", in Proc. 7th IEEE Consumer Communications and Networking Conference (CCNC) , January 2010, Las Vegas, Nevada. |
| [C1] | C. Tekin, S. Hong, W. Stark " Enhancing cognitive radio dynamic spectrum sensing through adaptive learning", in Proc. IEEE Military Communications Conference (MILCOM), October 2009, Boston, Massachusetts. |
Permission to reprint/republish this material for advertising or promotional purposes or for creating new collective works for resale or redistribution to servers or lists, or to reuse any copyrighted component of this work in other works must be obtained from the copyright holder.
Funding
- TÜBİTAK 1001 Program: Bayesian Satisficing: Theory and Algorithms.
- Outstanding Young Scientist (GEBİP) Award, Turkish Academy of Sciences.
- TÜBİTAK 1001 Program: Active Learning in Large Scale Vector Optimization Problems.
- Distinguished Young Scientist (BAGEP) Award, Science Academy Association of Türkiye.
- TÜBİTAK 3501 Career Development Program: Optimal Decentralized Cross-Layer Learning in Cognitive Radio Networks.
- TÜBİTAK 1003 Program: Improving Quality and Efficiency of Clinical Processes by Learning from Big Health Data.
Projects
Bayesian Satisficing: Theory and Algorithms
Program: TÜBİTAK 1001 ProgramProject Summary:
Machine learning has started playing an existential role in solving sequential experimental design (SED) problems that pave the path toward new scientific discoveries and breakthrough engineering products. Searching for an efficient design requires navigating through complex search spaces via sequential experiments. After several decades of tremendous research effort, Bayesian optimization (BO) is shown to be a promising tool for real-world SED problems. However, the search for the optimal is often futile due to the immense complexity of the objective function and design space and distribution mismatches that are prevalent in real-world problems. Therefore, BO falls short of addressing key performance objectives: sample efficient, accurate, and robust identification of efficient designs. This project aims to open a new frontier of research by formalizing the search for an efficient design from the lens of satisficing, an alternative model for rational decision-making pioneered by Herbert Simon, which can be described as achieving a satisfactory target utility under uncertainty. The Principal Investigator (PI) will form the foundations of the theory of Bayesian satisficing (BS) and study information-theoretic limits of design identification. The PI and his team will develop novel acquisition strategies that will achieve orders of magnitude improvement in performance objectives compared to the best BO methods. This requires establishing new acquisition functions and new techniques to deal with radical uncertainty and distribution shifts. The entire theory will be tested on challenging tasks such as molecular optimization, neural architecture search, and diabetes management. Tools developed as a part of this research will be made readily available to other researchers and practitioners via an open-source library and benchmark suite.
Active Learning in Large Scale Vector Optimization Problems
Program: TÜBİTAK 1001 ProgramProject webpage is here.
Project Summary:
Many complex scientific problems, including vaccine development for pandemic diseases and deep neural architecture search, require identifying optimal designs that satisfy certain performance criteria from a design set that includes many alternative designs via sequential experimentation. This problem has been mainly investigated in the literature when there is a single performance objective to be optimized. It has been studied under the names active learning, Bayesian experimental design, Bayesian optimization, etc. Due to their complex nature, many real-world applications of active learning require the optimization of multiple objectives. However, finding a design that simultaneously maximizes each objective under this setting may not be possible. Therefore, for the experts to determine which designs to focus their research on, it is necessary to identify Pareto optimal designs that are not dominated by other designs.
It is very difficult for domain experts to design optimal sequential experiments for problems that involve large design sets, multiple performance objectives intricately tied with each other, and restrictions on observations of design performances such as partial and noisy observations. The goal of this project is to design active learning algorithms that are mathematically rigorously founded, provably efficient and scalable, for complex learning problems in which identification of designs that optimize conflicting objectives by sequential experimentation via using the minimum amount of resources is required, given that the performances of the designs under different objectives were unknown initially. The algorithms developed in this project will enable experts in various disciplines, ranging from biology to data science, to quickly identify optimal designs in a small number of evaluations and use the minimum amount of resources. The results of this project will pave the path for having efficient and fast solutions for many scientific problems in different fields that require many trials and a lot of resources.
Optimal Decentralized Cross-Layer Learning in Cognitive Radio Networks
Program: TÜBİTAK 3501 Career Development ProgramProject Summary:
Cognitive Radio Network (CRN) is defined as a wireless communication system that is aware of the changes in its surroundings and that adapts its transmission parameters according to these changes. The goal of a CRN is to use the radio spectrum as efficiently as possible while operating resiliently under a diverse set of environmental conditions. The goal of this project is to design new learning and adaptation based methods for CRNs. The learning methods that will be developed in this project will enable each CRN user and each CRN layer to learn the transmission parameters that will maximize the system’s performance over time with limited inter-layer and inter-user communication.
Related Publications:| C. Tekin and E. Turgay " Multi-objective contextual multi-armed bandit problem with a dominant objective", IEEE Transactions on Signal Processing, 66(14): 3799-3813, July, 2018. |
| S. Muller, C. Tekin, M. van der Schaar and A. Klein " Context-aware hierarchical online learning for performance maximization in mobile crowdsourcing", IEEE/ACM Transactions on Networking, 26(3): 1334-1347, June, 2018. | E. Turgay, D. Oner and C. Tekin "Multi-objective contextual bandit problem with similarity information", in Proc. 21st International Conference on Artificial Intelligence and Statistics (AISTATS), April 2018. | M. A. Qureshi and C. Tekin "Online cross-layer learning in heterogeneous cognitive radio networks without CSI", in Proc. SIU, 2018. |
| C. Shen, R. Zhou, C. Tekin and M. van der Schaar " Generalized global bandit and its application in cellular coverage optimization", IEEE Journal of Selected Topics in Signal Processing, 12(1): 218-232, January, 2018. | C. Tekin and E. Turgay "Multi-objective contextual bandits with a dominant objective", in Proc. IEEE MLSP, September 2017. |
Improving Quality and Efficiency of Clinical Processes by Learning from Big Health Data
Program: TÜBİTAK 1003 ProgramProject webpage is here
Project Summary: Big Health Data (BHD) has a great potential to support clinicians in diagnosis, treatment administration and patient monitoring. However, BHD includes a vast amount of documents, test results and medical images related to the past treatments of the patient. Leveraging this information requires development of sophisticated statistical learning techniques for diagnosis and treatment recommendation and risk management. The goal of this project is to design trustable machine learning algorithms that will learn to make optimal decisions using the BHD, and to integrate them into new decision support systems that will be used by clinicians and patients.
Software
Software related to selected publications can be found in our group's GitHub page.